In reality, dogs guard houses, prevent thieves and protect its owner. Keeping a watch dog like rottweiler, bulldog, or doberman to guard the house is definitely a good choice.
For computers, no rottweilers...:( BUT...let me introduce a watch dog call Scotty :D
I have been training Scotty for quite some time and notices that Scotty is a very loyal, smart, intelligent, high performance but sometimes irritating :(
Scotty is born in a company call BillP Studios, the product name is called Winpatrol
http://www.winpatrol.com/
Again, installation is as easy as ABC. Install winpatrol and say hi to Scotty. There is many things that Scotty can do, it can be used to clean virus. Some virus disable the task manager of windows, and hide itself from being detected by anti virus. Even if the virus did not disable the task manager, some virus is visible and can be seen in the task manager. You can end the process in task manager, but next time your when machine boots up, the virus will be execute again....:(
Using Scotty/Winpatrol u can actually view the folder/directory of the virus file.
for example, explorer.exe(not a virus, just an example, but some virus may use the same name)
Click on 'Active Tasks' ( In case some virus disable your task manager.This can be used to stop the virus) Right Click and click 'Info'
Now you can see the location of the program, if it is a virus, you can browse and find the folder then delete the virus folder or .exe file manually
Scotty can also view the startup location of a program or explore the folder, you can also disable some programs which you do not want it to start when booting up yr machine.
You can also view the ActiveX which is use by Internet Explorer or other browsers,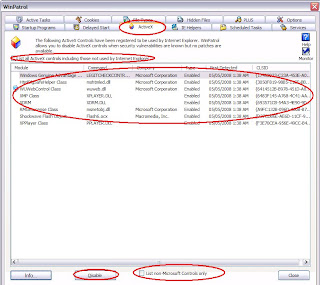
or view hidden files
This is a good program if you want to remove a virus manually or view processes that is running in your machine. Winpatrol will automatically scan your computer for any possible treat. If a virus is trying to modify your system files, winpatrol will alert you and ask wait for your decision whether to allow or decline the changes.
Scotty will keep on scanning and alert you if there is any changes in your system.
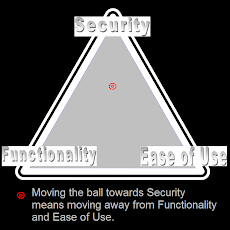
So, performance or security? :) Triangle...........
25 June 2008
Keeping watchdog in your computer
Posted by Lucas™ Pang at 8:52 PM 0 comments
20 June 2008
Storing your private files - Encrypted!
Have you ever wonder how you could store your private files safely in your computer? If there is only one user of cause with a strong password that I showed you, you can protect your private and personal files. What if there is more than one user and both of you are using the same user account?
One "traditional" method is to use third party softwares like Folder Lock. Folder Lock is a shareware software that you may have tried, it can be use to protect your personal files. When I first saw folder lock it 'looks safe', Folder Lock's user usually end up in 2 situations:-
1)Forgot their password
2)Expired! lol! After the trial period, data are still in the 'protected' folder (if the user did not purchase the software)
But believe me this software is too lame, it can be compromised, easily...:D
Many people are not aware of that, and not many people knows how to crack the password. So it is still consider safe...but since there is chances of being compromise, so forget about Folder Lock now.
OK....SOLUTIONS?
TrueCrypt - FREE!!! :D
http://www.truecrypt.org/
This software automatic encrypt your data that is stored in the hidden drive. This software works the same like folder lock, the reason I introduce this software is because it have not been compromise...yet
Now, I'm not going to demonstrate how to install it. The installation process is easy. After you successfully installed TrueCrypt; You should see this,
Click yes if you want to view the tutorial, after clicking you will be automatically redirected to their website.
Click Create Volume and the wizard will guide you, Click 'Create a File Container' and 'Next'
Now select a volume type. (I am going to select 'Standard TrueCryt Volume to demonstrate)
Click 'Select File' and select your volume location, I will name it 'My Volume'

Click 'next'
Select The Encryption Option and click next,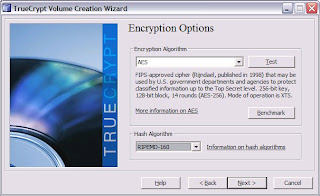
Now key in the Volume Size, and the password.

Select the Type of File System and Click 'Format'
Click 'OK' and 'Exit'
Now, Click 'select file' and select the volume,
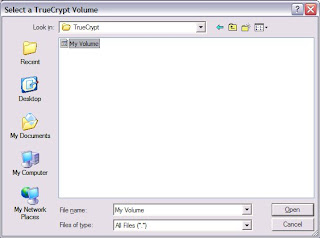
Click mount and key in the password,
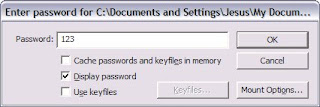
Now go to My Computer and you will see that mounted drive,
Now u can save your private or personal files here, i have created 2 files for testing,
To hide the drive, Click 'Dismount'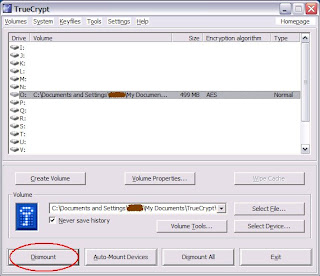
now go to my computer, you wont be able to see the Drive because it is hidden and it can only be seen after u mount it, after dismount, try to mount it again to make sure your files is not lost....
*To mount it, you have to repeat the step of selecting the volume file and mount the drive
*Before you reinstall your windows or any Operating System remember to backup your files that is in the protected drive.
*Remember the location of the volume file and your password.
This software is still consider safe, but believe me, one day it will be hacked....lol
Posted by Lucas™ Pang at 3:13 AM 0 comments
16 June 2008
Windows can get infected just by viewing a Web page
Yes! It's true. By just browsing web pages, your computer can get infected. The old "myth" of not opening email attachment doesn't works anymore today, by just reading e-mail message can infect windows.
When you are browsing web pages using your browser, once you type in the address,
The page is loaded for you in your computer, but where is the content stored?
When you are browsing web pages, the image is stored in the temporary folder in
"C:\Documents and Settings\USERNAME\Local Settings\Temporary Internet Files"
So it means, the image is stored somewhere in that folder, the image may contain malicious software like virus, spywares, worms, Trojan and any unwanted stuff that may harm your windows. Malicious software doesn't need to be attach to image, it can come directly to your computer without attaching to any file.
When these malware (malicious software) are already in your computer, some virus can run without being detected by your antivirus, some hackers might install key logger in your computer, monitoring your keystroke.
So, SOLUTIONS?
McAfee Site Advisor
http://www.siteadvisor.com/
Log on to siteadvisor.com, download SiteAdvisor. It works for IE and Firefox.
Once you have installed, (I am using Firefox to demonstrate)
Click on it and go to settings,
Select, "Highlight search result links" and "Use SSL communication to server"
and now, try to search something in google
click on the (X) and No. of red downloads, the results...
click on any of the virus found,
and lets see what the "free stuff" will do to your computer,
So, try it out! It is one of the way to prevent u from being infected.
oh ya, always remember,
"Moving towards security means moving away from functionality and ease of use"
Posted by Lucas™ Pang at 10:27 PM 3 comments
14 June 2008
A Strong Password
Before I go further, i want to remind my readers that it is very important to have a secure password. Password will protect user's computer from unauthorized people or maybe a connection. A strong password will definitely strengthen your computer's security.
The length of a strong password that i recommend should be at least 15 Characters long. Because the softwares that a hacker use are usually from the internet. Most of the password cracking software that is available to the "hackers" could only break 14 characters. That is why i recommend my readers to use a password that is more than 15 characters.
Instead of using alphabet only you can use a combinations of alphabet, numbers, symbols, uppercase and lowercase for example:-
defensivecomputing
DeFeNsIveCoMpUtInG
D3F3N51VeC0m9Ut1N6
D3F3^$!V3(0M9uT!^G
d3F3^$1v3(0M9Ut!^G
Instead of using password, we can use pass phrase, for example:-
thequickbrownfoxjumpsoverthelazydog
ThEqUiCkBrOwNfOxJuMpSoVeRtHeLaZyDoG
Th3Qu1(k8R0wNfo#7uM9$0^3rT#e!42yDo6
So, there is a lots of ways combining alpha, numeric, symbols, signs, uppercase, lowercase. Since pass phrase is so long you can always play around changing and replacing the alphabet with other symbols and signs. If u feel that pass phrase is too long and u cant remember that password, another example that i would give is :-
TheQuickBrownFoxJumpsOverTheLazyDog
so, TQBFJOTLD (try to make it to at least 15, this is just an example)
Now use the same way like above, replace the alphabet with symbols and signs. Use combination of uppercase and lowercase. A few more things that i need to highlight before i end this session :-
1)>15! >15! >15!
2)Don't use words that can be found in the dictionary like: apple,boy,cat,dog. use a password like TQBFJOTLD which is not an English word and it doesn't make any sense.
3)Never use the same password for every account, user name or email address.
4)Change yr password frequently, at least once a month, try to write down and put it in a safe place in case u forgot the password.
5)QWERTYUIOP or 123456 is not a safe password....remember that...
6)Don't use password that is the same with the username, like admin or root.
7)Avoid using password that is easy for hackers to guess, like your birthday,name,IC no., Lucky number,Idol's name and words that u often mention in front of people, things that u like, your hobby...
Ok, I hope you have understand about the ways to strengthen your password and what is a strong password....TQ
Posted by Lucas™ Pang at 1:08 AM 0 comments
08 June 2008
Introduction to Computer Security
Let me start with a quote,
"No system is 100% secure"
Don't tell me that your system is 100% secure because,
"I am not connected to the internet" ><
Some hackers could easily hack your computer system in just a few seconds by just using a USB thumbdrive if he has physical contact with your computer system.
Later on, I will demonstrate it in a post how to prevent yourself from being a victim of that threat. To make my readers easier to understand, i will try to make more snapshot and provide some links to for reference. and, always remember the triangle...
I will first start with some basic softwares which you can get for free to secure your system first, these software might looks normal but it do helps, because i have experienced it, trying and testing it before i post it here.
We will go step by step, my primary aim is to help home users, for enterprise and corp. it will be totally different way and environment to protect their system.
People who is not a computer literate, i would recommend them to visit my blog for tips and people who think their computer system is secure, they should think 10 times before they say,
"My system is definitely secure"
Copy any content here, share with your friends, post it in your blog, reproduction is not prohibited here, but credits to me please... ><
Posted by Lucas™ Pang at 2:43 AM 0 comments